The growth of cloud infrastructure in recent years has led to a surge in popularity of Software as a Service (SaaS) packages such as Microsoft Office 365. This popularity stems from a variety of factors, including ease of use, reduced costs, and automatic updates. In fact, we are seeing more and more the following:
- Time spent in Microsoft Teams meetings has more than doubled globally, increasing 148%.
- The average Teams user is sending 45% more chats per week.
- The number of emails delivered to Microsoft 365® customers went up by 40.6 billion between Feb. 2020 and Feb. 2021.¹
- There was a 66% increase in the number of people working on Microsoft 365 documents in the past 12 months.
So in short, we know that hybrid working is here to stay. Recent survey showed that 73% of employees want flexible remote options to stay/be permanent and 66% of business decision-makers are thinking about redesigning physical spaces and IT networks to better accommodate hybrid work environments. Keeping that in mind, businesses are now poised to have increase exposure and risk if the proper steps are not taken to secure this on-demand data that is being shared across many users within the network. As a result of this surge, 77% of companies that use SaaS applications suffered a data loss incident over a 12-month period.
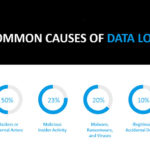
What oversights are commonly seen that result in this type of data loss?

Below are some real work examples of how each of these pillars can happen:
- Employees inevitably delete the wrong email, contacts, or critical configurations.
- Microsoft will honor your deletion request without question. They have no way of knowing if it’s a hasty (or malicious) request and they are not – responsible for any unexpected results. In short, Microsoft is not responsible for your data loss. You are!
- These powerful tools designed to streamline business processes can ruin critical data in a flash — with no undo if no measures are put in place such as automatic back ups, etc.
- Employee action is involved in up to 23% of all electronic crime events
- Rogue software can spread mayhem with programmatic efficiency without an active attack from a hacker. Many malware programs and viruses emerge from existing code after hibernation, making them especially hard to defend against.
Now knowing human error and malicious attacks are major causes, who is really responsible for your data then? You or Microsoft?
In short, its a shared responsibility.
The fact is Microsoft is only responsible for Hardware and Software failure along with any outages within their network & infrastructure. Any other factors such as human mistakes, programmatic errors, malicious insider activity, external hackers and access & permissions control issues all come under the business’s responsibility. As they say, read the fine print in Microsoft’s service level agreement which states:

So what steps can you do to ensure you data is always protected?
Well first and formeost is to have a robust cybersecurity IT strategy and plan in place where IT professionals, like ThirdPowerIT, can put technologies and best practices in place to prevent as much breach and human error as possible. Secondly is to have a back up disaster plan in place that automates your back ups with a quick recovery.
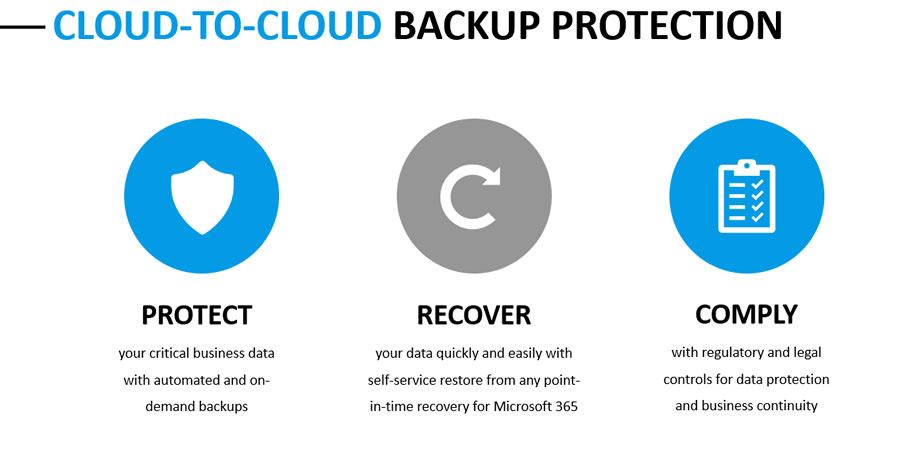
Here at ThirdpowerIT, We Can Help Protect All Your Microsoft 365 Account Data With:
- Automated Backup s
- On-demand Data Restore & Recovery
- Granular Point-in-time Recovery
- Ability To Reestore Flexibility for Admins, Users and Devices
- Provide Transparent Reporting (Audit Logs)
- Ensure Your Data Centers Are Located Globally
Also, depending on your industry regulations and the type of data you store, we ensure you are compliance in all aspects HIPAA, PCI, NIST & more.
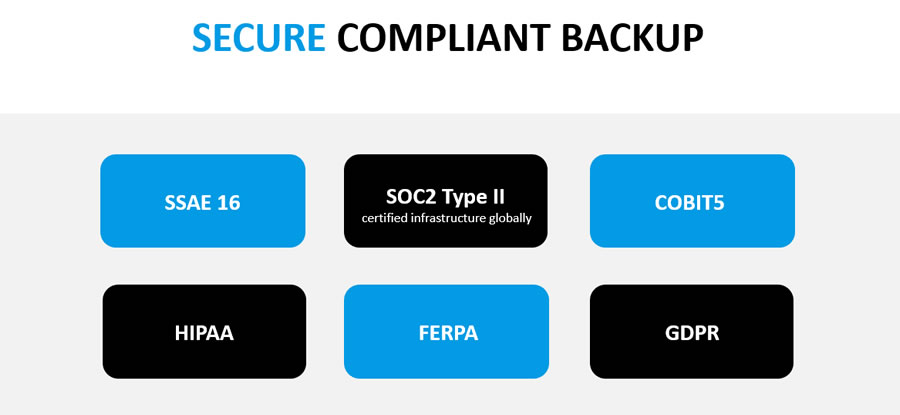
How Secure Is Your Data?
Not sure? Getting started is easy. Give us a call or click on the button below to schedule your FREE 30 minute consultation and learn how we can put in a strategy that protects your data the way it needs to be.
The post Secure, Reliable Protection for Your Microsoft 365 SaaS Application Data appeared first on Third Power IT – Managed IT Services.
Courtesy of Miami IHIPAA Compliance IT Company - ThirdPowerIT.com